Ok here is a little tip when trying to add trusted root certificate authorities to Skype for Business 2015 and Lync 2010/2013 Edge servers.
Microsoft have a list of Unified Communications Certificate Providers detailed here: https://support.microsoft.com/en-us/kb/929395
Windows now automatically downloads Trusted Root certificates when you access a web page on HTTPS. We can exploit this to get all Trusted Root certificates on our Edge servers which is required for Federation to work correctly. An example of this is where you only get one way IM or a federated partner may see your presence as unknown.
First of all you need to allow HTTPS (TCP/443) out from your Edge server(s). If you don’t want to bug the Firewall admin you can stop SfB/Lync Services (Stop-CsWindowsService) and remove the Access and Webconf IP addresses from the external NIC. The AV Edge IP should already have TCP/443 outbound.
Next you need to open up Internet Explorer and navigate to the HTTPS site of each Certificate Provider in the list provided by Microsoft, e.g.:
https://comodo.com
https://digicert.com
https://www.entrust.net
https://geotrust.com
https://www.globalsign.com
https://godaddy.com
https://symantec.com
https://thawte.com
https://wisekey.com
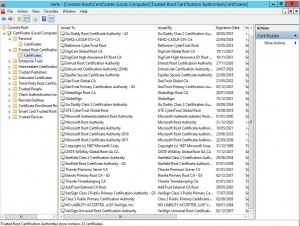
Once complete you will see that Trusted Root Certification Authorities is now populated:
If you have removed your Access and Webconf IPs from the external NIC, re-add them and start the SfB/Lync services (Start-CsWindowsService)

Technical Architect

Pingback: One Liner: Add Trusted Root Cert Authorities to Edge Servers - Ehlo World!
Cool method. I played with this in PowerShell and came up with a way to automate it. See http://www.ehloworld.com/3029.
Hi What name should it be on the added root certificate after I browser symantic.com? When I check the root certificated I can´t see the name. The reason I ask is that I have alarm 14603 even after I add the domains to federated. The common issue to the alarm is that every external federation domain uses Symantec certificate.
Hi Daniel,
You should have a VeriSign certificate in the Root store. You may also have a Symantec Class 3 EV SSL certificate in the Intermediates store.
I’ve found that Federation doesn’t work correctly when Certificates are in the wrong stores. You could try deleting all “VeriSign” and “Symantec” certificates from the Root and Intermediate stores. Navigating to https://symantec.com will put the correct VeriSign root cert into the Root store.
Chris